Dear @gevs, @BloodyRookie (and other NEM tech wizards),
cc. @jtey1 (LuxTag) and @musdom (LuxTag)
We at LuxTag are working on un-copyable tags using NFC embedded Hardware Security Modules which do the cryptographic signing. They keep the randomly generated private key inside the chip and do the signing, similar to common crypto hardware wallets.
Recently, we spoke to a manufacturer to check on compatibility with NEM cryptography, so that the signing could happen on-chip.
- They said their chips are compatible with the common cryptography and as such with the main blockchain projects. They call NEM an “exotic blockchain”.
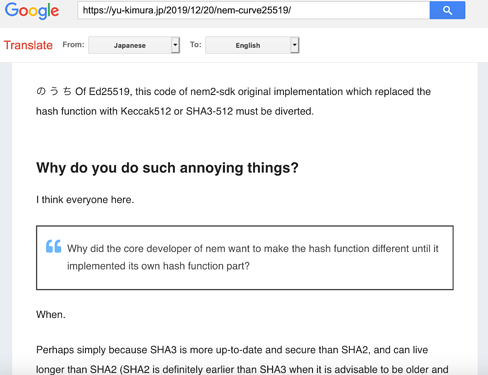
- They said that NEM 1.0 would be able to work with minor tweaks, as it uses ED25519 SHA2-512.
- NEM 2.0 (Codenames Catapult, Symbol) would not work as it deviates from industry standard. To my understanding, this relates to the use of SHA3-512.
- The chip manufacturer seems to advise us to change from the “exotic and incompatible blockchain NEM1 / NEM2” towards a more mainstream platform.
 (Allegedly, even Hyperledger Fabric and others are out-of-the box compatible)
(Allegedly, even Hyperledger Fabric and others are out-of-the box compatible)
Can I ask for opinions and recommendations regarding the hardware module signing (hashing/signing) for NEM 2.0?
Thank you and happy 4th advent sunday  .
.
( https://www.german-way.com/history-and-culture/holidays-and-celebrations/christmas/advent/ )
Rene, LuxTag.io