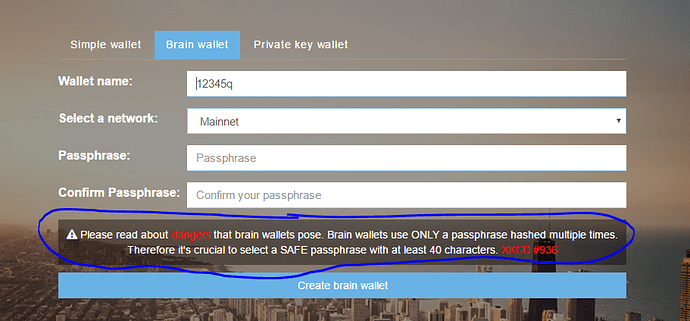
If you happen to land on a malicious website with your wallet loaded and not yet purged.
My understanding is that they already have stolen many wlt-files that way. brute forcing is just a matter of time unless a password as good as the private key is being used. my weak password took them 5 days.