@gimre shared a very interesting forum post on the JP side of Catapult demonstrating the use of the new secret lock transaction for an atomic, cross-chain swap:
I found this quite interesting. I found it even interesting that there weren’t many posts in this forum. In response to that I have decided to start a series of posts called Catapult 101, where I break down various Catapult concepts for the layman to understand 
I don’t only want to discuss it, but demonstrate it using NEM2.
Here is the first installment from the aforementioned article, in proper English so we can discuss it!
Thanks to @memario for clearing up a few things that were misrepresented in this article 
Using secret lock transactions for atomic cross-chain swap.
Introduction
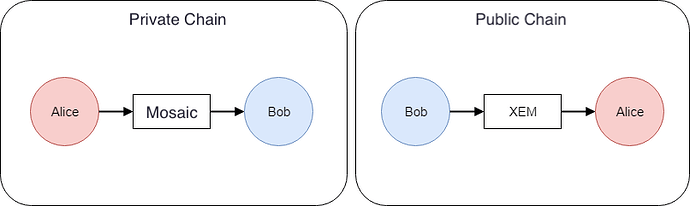
Suppose you have two different MIJIN_TEST chains. A "Public Chain" (i.e NEM) and a "Private Chain" (i.e crackTheCode Chain), respectively. Let's refer to the private chain as `A` and the public chain as `B`
Bob wants to send XEM to Alice from her A chain, and Alice wants to send Bob a mosaic from his B chain.
In short, they want to perform a cross-chain transaction, exchanging XEM for a mosaic (or vice versa)
Now, if Alice and Bob both trust each other with no problems, then they can simply peform a transfer transaction on each chain.
In our scenario, however, they don’t trust each other. This is where secret lock transactions come into play!
Secret lock and proof transactions
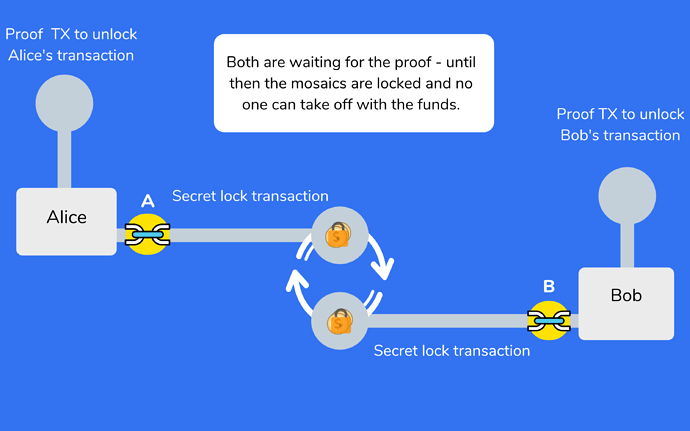
This is where the secret lock and proof transactions come into play in a trustless environment as stated here, where mosaics are locked, or unlocked, with a secret value only shared between Bob and Alice.
There is no trust because Bob could take off with Alice’s mosaic without sending his. The secret transaction essentially holds it in escrow until both secrets are entered in their respective chains. If the secret is never entered, the funds get returned to their owners.
Like a transfer transaction, a secret lock transaction can send mosaics. The difference, however, is that it has to be unlocked via a secret proof transaction.
A secret lock transaction has a hash of a secret value embedded within it, similar to a message. If you can prove that you know the secret value via a secret proof transaction, you can receive the mosaic being sent.
It requires the common secret shared between the two parties (Bob and Alice) to unlock.
Here is how an atomic transfer might go:
-
Alice creates a secret lock transaction on the private chain that sends a mosaic to Bob’s address. A secret is included in this transaction
-
Bob receives the transaction and the secret. He now announces a secret lock transaction with XEM with on the public chain. This transaction uses the same secret that Alice sent to him.
-
Now that we have a secret lock transaction on each network, they must be proven by each party. Alice sends a secret proof transaction to Bob on the public network where she wants to receive her XEM. Bob does the same on the private network where he wants Alice’s mosaic. Once this occurs, and everyone has sent their transactions in due time and nothing has timed out, the transaction is concluded!
-
With the transaction concluded, Alice has her XEM on the public chain and Bob has his mosaic on the private chain!
As you can see, this type of cross-chain exchange is possible. In total four transactions are required to make this transfer. Secret lock transactions help to avoid fraud if one or more parties do not trust each other.
The possibilities - not just currency exchange
While here a cross-chain exchange was performed, this method can be used to communicate between chains through sending messages, or even for holding funds in escrow between a private chain and public NEM chain for a house purchase until the deal is closed! There are many ways this can be utilized :smile:
Now see how you can try it out yourself!
Coming soon